A Beginner’s Guide to Cyber Security - What's It All About?
Unfortunately, there’s no escaping the figures of cyber-crime, but there are steps that you (as an individual, small business, or large business) can take to ensure that you understand cyber security, and how best to avoid a cyber-attack.
In 2017, 37% of U.K. businesses experienced at least one cyber security attack. Over the years, attacks on small businesses have grown exponentially, with 18% of small businesses being targeted in 2011, and 43% in 2015.
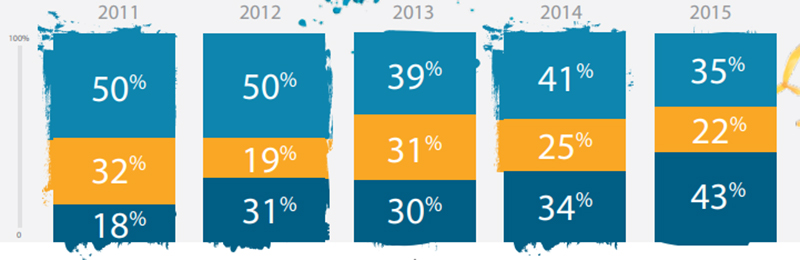
Credit: Symantec.com – Attackers Target Both Large and Small Businesses
We’re going to cover some of the common technological jargon that’s used, what it means, and how to protect yourself from becoming a victim.
1. Data Back-ups
Whether you’re an individual or business, it’s really important to back up your data; from images to files, databases to customer information. If you do fall victim to a cyber-attack, you’ll at least have your important data kept safe and accessible. The question is, how are you going to back-up such a potentially large amount of data? You could save your data onto a portable drive like a USB stick or external hard-drive, however, you’d still be at risk from a possible cyber threat.
Ransomware, or malware, is a piece of software that can access your data, on your computer, phone, or tablet – a ransom must be paid if you want your data back, or you’ll be blocked from accessing it, and it may potentially be leaked for the world to see. Certainly not a good thing if you’re a business holding customer information! These cyber attacks can leak onto your physical hardware; even portable drives.
2. Cloud Storage
By now, you’ve probably heard the term ‘the cloud’ or ‘cloud storage’ floating around; but what is it exactly? Without even being aware of it, if you use an email client, you’re already using the cloud to store your emails. Cloud storage is a brilliant way to store your data in a non-physical location, making it a much harder target for cyber attackers. With a higher level of flexibility and availability, cloud storage is becoming a staple part of most personal and business storage solutions.
Many people don’t realise that web hosting companies, such as these, also provide cloud web hosting, meaning your personal or business website, including its data, storage, and databases can also be hosted and stored on the cloud. Again, this provides a lot more flexibility in terms of storage, even if you experience more website traffic and data than you expected, and are much less prone to cyber threats and attacks.
3. Antivirus Software

Although most computer systems and mobile devices now come pre-built with antivirus software to protect against viruses and malware, it’s important that you ensure all of your devices are protected. Most antivirus software packages available can be used on multiple devices, but often do come at a price – a price that’s certainly worth paying for to keep you protected. It may seem obvious, but making sure your antivirus software is turned on is key to ensuring you’re not inviting hackers to attack your hardware.
If you manage a business, you should ensure that your staff have permissions to perform their role sufficiently, without additional permissions to download external apps (unless required). Third party software is often the cause of viruses being leaked onto devices, so restricting staff access may be a necessary step to take to ensure that they can’t download any potentially harmful applications onto their computers.
4. Password Protection

We know it can be frustrating trying to remember a different password for all of your devices, logins, etc. however, it’s so important to make sure you create a password that contains special characters, numbers, and capital letters to make it more difficult for potential hackers.
Two factor authentication (2FA) is a method by which you must prove 2 forms of identity before logging into a system; whether it be an application or device, 2FA is a great source of protection. Again, it can be tiresome, but much less so than opening yourself up to a potential cyber-attack. 2FA often requires a password and a code, or fingerprint in order to grant access; if the opportunity arises to enable 2FA on your device, take it.
This may be an obvious remark, but ensuring that your passwords are hard to guess are key to your protection; don’t include your pet's name or a word that might be easy to guess based on who you are, and never give your password to anyone! To secure login credentials, there is another way to secure the data transferring between the server and the browser called SSL certificate either it is a regular or any type of digital certificate, it always secures the details between two ends. For example, strong security is needed when it is a question of securing unlimited subdomains. In this case, a cheap wildcard SSL certificate can be of great help here. A cost-saving feature with other important elements makes it worthful.
5. Phishing Attacks

Phishing attacks are often seen in the form of emails, requesting the user to provide sensitive information such as personal data, bank information, or click on links to harmful websites. Phishing emails can be hard to identify, so we’ve put together a few tips to help you out:
- A lot of phishing attacks mask themselves behind well-known company names or organisations. If you receive an email from an unknown source, it’s best to treat it with suspicion. If you’re being asked for personal information and you as an individual or company have never dealt with the organisation before, do not respond.
- Take note of the email address that the email has been sent from; most phishing emails hide behind a randomised email such as [email protected] – a lot of these email addresses can be easily identified as spam, however, if you’re not 100% sure, you can always contact the company directly, through official means via their website, if they’re a recognisable brand. Otherwise, simply ignore the email and delete it.
- Keep your eye out for punctuation and grammar mistakes in suspicious emails; a lot of these scams come from overseas, and are easy to spot due to the way their emails are presented.
Being aware and alert of potential cyber threats is often the best way to protect yourself from them. If you run a business or company, there are plenty of valuable sources available that you can use to train your staff – an hour out of your working day to educate your team members could be more valuable than you could imagine. Taking simple measures doesn’t mean that you’re not taking cyber security seriously; the most basic protection could protect you from basic attacks, and is a good starting point for any individual or organisation. Don’t be afraid to invest money into reputable software – it could save you from a cyber-attack, and is absolutely invaluable.
Related Posts
Tech Support is also known as Technical Support Services.According to a common description, it is generally used to supply technology-related assistance to the users of pc, laptops, smartphones, televisions, or various software, electronic and mechanical products.
It’s essential to keep your website secure even if you don’t have any sensitive data that needs to be protected. Keep reading to find out more about the best practices for website security.
Identity theft and account takeovers are prevalent nowadays. Here are some measures you can apply to prevent payment fraud on your website.
Everyone is welcoming technological innovations with open arms. Entrepreneurs are reaping benefits of online marketing, while customers are happy to make online payments.
All it takes is for a simple hardware malfunction to destroy your entire computer and everything on it. Learn how to backup data on the Mac to prevent this.

















Comments
comments powered by Disqus